It's hard to believe it's been a whole year since Mobility Field Day 11, where Juniper made some huge announcements that I wrote about. What a ride it's been since then! This year, I was honored to be invited to be a delegate at Mobility Field Day 13 because of my coverage of Mobility Field Day 11. As a delegate, I was in the room when Juniper Networks continued its track record of making awesome announcements. Juniper had a packed 3-hour session where they covered some significant enhancements coming soon! These upcoming releases continue to extend the Mist portfolio in some great ways.
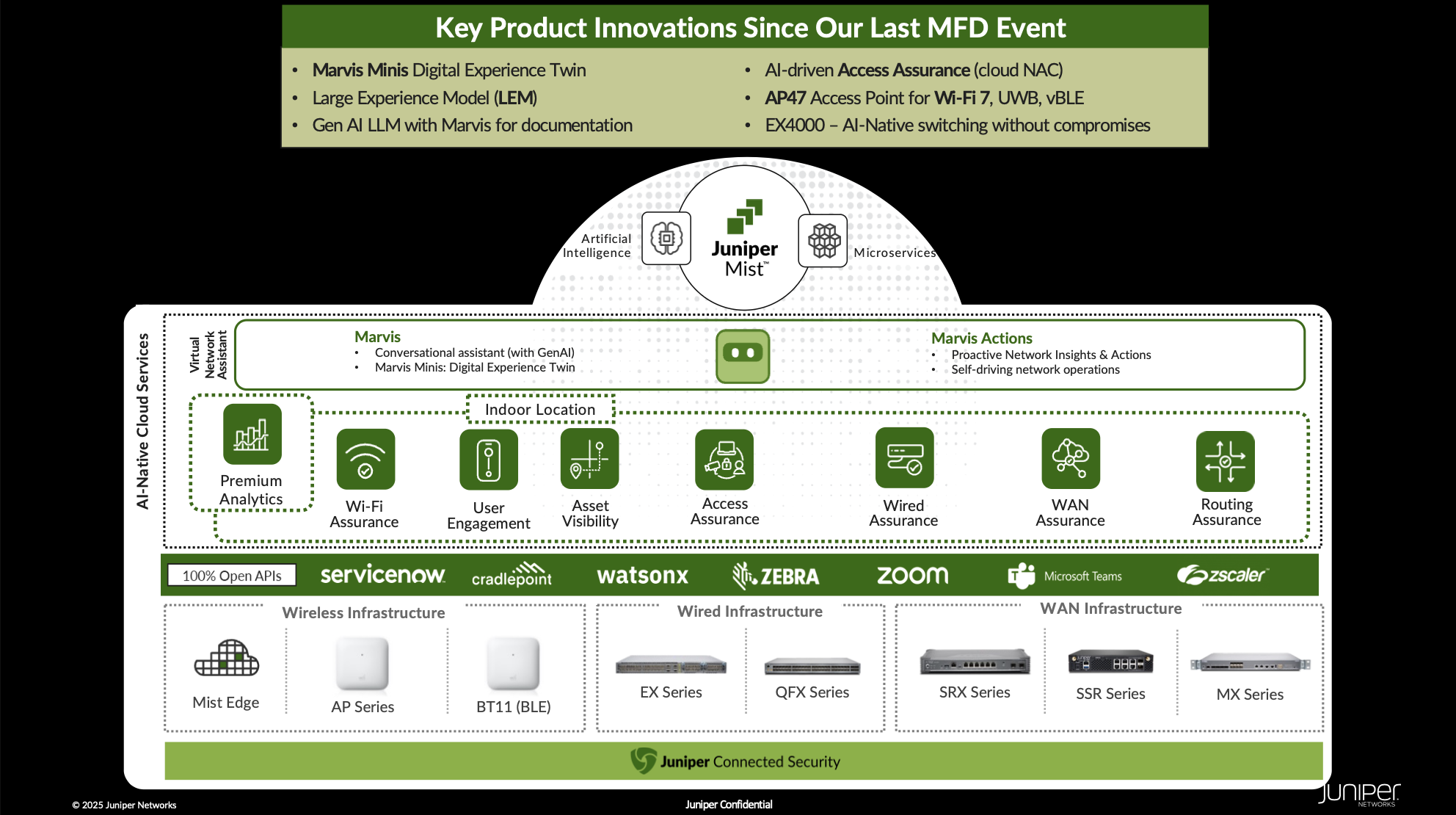 Before we get to the specific announcements, though, it was great to get an overall update on how things have gone for Juniper in the last year. It started with Sujai Hajela giving an overview of the momentum that Juniper Mist has been gaining in the last year. Then Bob Friday showed us how, over time, Juniper continues to improve on its AI featureset. And that while there is a lot of use of the "AI" term around the networking industry, Juniper is really delivering in ways that make sense and growing at a controlled pace, not just chasing the "buzzword of the moment". Another highlight (as always) was hearing from Wes Purvis about 6GHz, real-world information on the age-old 2x2 vs 4x4 AP discussion, and why a directional Wi-Fi 7 AP was important to release. He also discussed some changes to the Radio Resource Management (RRM) algorithm to improve it. While we've come to expect big things from the product side of things at Mobility Field Day from Juniper, getting these more general information sharing updates is always refreshing. So, let's queue some Sudheer Matta energy and get into the announcements!
Before we get to the specific announcements, though, it was great to get an overall update on how things have gone for Juniper in the last year. It started with Sujai Hajela giving an overview of the momentum that Juniper Mist has been gaining in the last year. Then Bob Friday showed us how, over time, Juniper continues to improve on its AI featureset. And that while there is a lot of use of the "AI" term around the networking industry, Juniper is really delivering in ways that make sense and growing at a controlled pace, not just chasing the "buzzword of the moment". Another highlight (as always) was hearing from Wes Purvis about 6GHz, real-world information on the age-old 2x2 vs 4x4 AP discussion, and why a directional Wi-Fi 7 AP was important to release. He also discussed some changes to the Radio Resource Management (RRM) algorithm to improve it. While we've come to expect big things from the product side of things at Mobility Field Day from Juniper, getting these more general information sharing updates is always refreshing. So, let's queue some Sudheer Matta energy and get into the announcements!
1. Marvis Minis Go Global
I really love the Marvis Minis feature in Mist (so much so I've printed over 500 Marvis Minis to give away since they were announced!). If you're not familiar, Marvis Minis is the name of Juniper's synthetic testing and user experience monitoring feature. This testing is performed by the APs themselves, localized (so per VLAN) as if it were a client connection to the AP. This allows the minis to test the client experience from the AP outwards. All of this data feeds into the Mist AI and allows Marvis to recommend remediations for any issues it finds, even without clients at the site. Up until now, this testing has been viewed mostly on a per-site level. You can view and track this information at the organization level, but that was more of a high-level "how're things doing at reach of my sites".
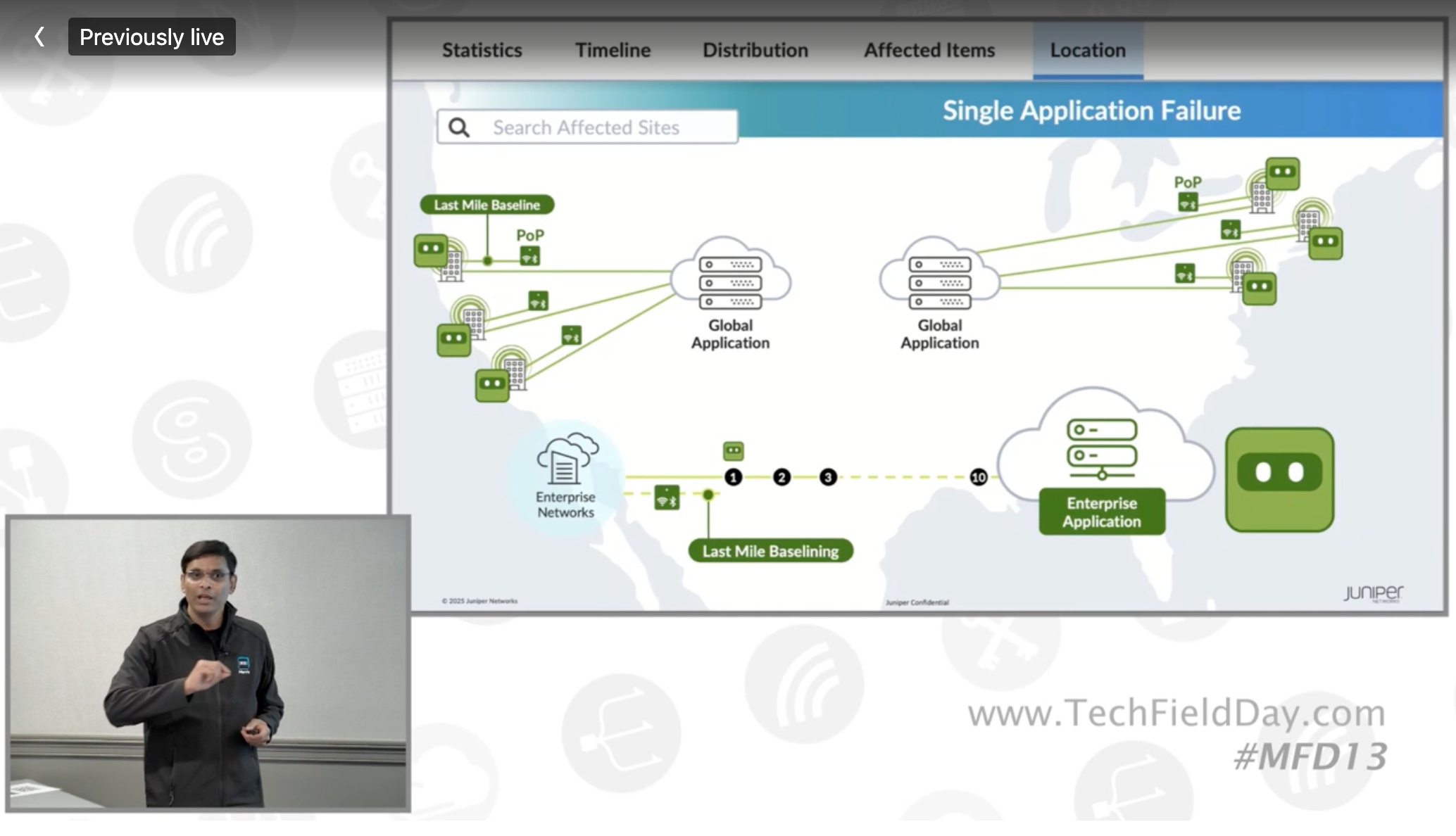 And this new release has Marvis Minis "going global!" What does that mean? Well, in this case, it means that Juniper will be running Marvis Mini data workers in regional points of presence (POPs) around the globe. These workers will enable gathering additional data to give Marvis insight into where there might be problems. The data will be correlated with individual client data to gather information on last mile, regional outages, etc. For example, if a site is seeing high latency, today Marvis could show you there is a latency issue on the WAN circuit. With this new feature in place, Marvis could tell you that there is a regional outage, or that the latency issue lies between a regional POP and your site (i.e., the last mile). This added insight helps you know if there is something that you can do (in the case of a last-mile issue) or not (a regional outage). It can also tell the difference between a single application issue, multiple applications, etc. One of the best parts? This updated feature is not a new license; it's included in the current Virtual Network Assistant subscription. This is just one of the reasons I really advocate to my clients who are purchasing Mist to always purchase the VNA subscription. While there is a "cheaper" option to only get a Wireless Assurance subscription (single sub), I think you're really missing out on a key differentiator between Juniper Mist and their competitors when you do that.
And this new release has Marvis Minis "going global!" What does that mean? Well, in this case, it means that Juniper will be running Marvis Mini data workers in regional points of presence (POPs) around the globe. These workers will enable gathering additional data to give Marvis insight into where there might be problems. The data will be correlated with individual client data to gather information on last mile, regional outages, etc. For example, if a site is seeing high latency, today Marvis could show you there is a latency issue on the WAN circuit. With this new feature in place, Marvis could tell you that there is a regional outage, or that the latency issue lies between a regional POP and your site (i.e., the last mile). This added insight helps you know if there is something that you can do (in the case of a last-mile issue) or not (a regional outage). It can also tell the difference between a single application issue, multiple applications, etc. One of the best parts? This updated feature is not a new license; it's included in the current Virtual Network Assistant subscription. This is just one of the reasons I really advocate to my clients who are purchasing Mist to always purchase the VNA subscription. While there is a "cheaper" option to only get a Wireless Assurance subscription (single sub), I think you're really missing out on a key differentiator between Juniper Mist and their competitors when you do that.
While I don't think this feature release is "ground-breaking," I do think it's an important step forward. The added visibility that will come from Juniper injecting more regional data into the models will be a great way for clients to see more precisely where the problem they're experiencing is. By tracking this as a Service Level Expectation (SLE), they will also gain trending over time. When you're dealing with local carriers, this level of data and visibility can really push them into resolving a weird local issue. Or if it's regional, you can save an administrator's time trying to find the status page for the carrier, app, etc. And by doing this under the same subscription, folks should already have it, it really continues to add value to that subscription (where some people have said they didn't see as much as others).
2. Large Experience Model
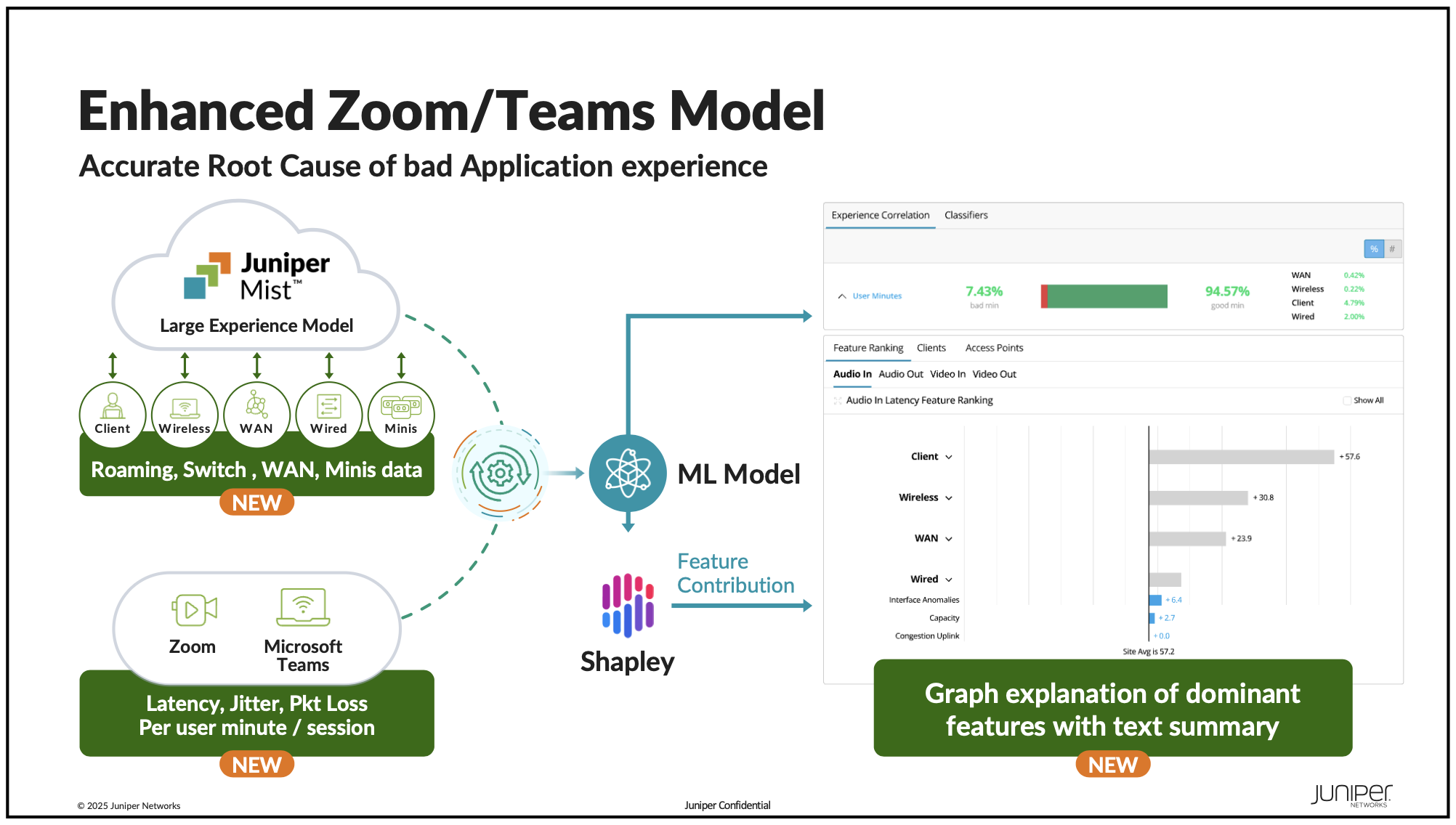 It's been a little over a year since Juniper announced its integration with Teams and Zoom. This cloud-to-cloud integration allows Mist access to client-level data from the individual users' application client. In the dashboard, Mist administrators can compare network data to the call data, and use Marvis to determine where some of the issues may have been during a problematic call. This feature has been really helpful for some of my clients who have used it to track down issues with their Teams and Zoom calls. But I have other clients who don't use Teams or Zoom for collaboration and were looking for something similar to this for their various apps. Well, that may still come, but the second big announcement Juniper made was for a Large Experience Model (LEM). This model builds on the data they have gathered and allows the next step of making predictions of application performance. So, rather than just saying "during this call there was a problem because of latency on the WAN link" with the LEM, you can say "it's expected that, based on this network information, calls here will be problematic because of WAN latency". And this predictive capability doesn't require Zoom/Teams integration, nor is it limited to Zoom and Teams applications. And all of this data will be presented in a new Service Level Expectation (SLE) section.
It's been a little over a year since Juniper announced its integration with Teams and Zoom. This cloud-to-cloud integration allows Mist access to client-level data from the individual users' application client. In the dashboard, Mist administrators can compare network data to the call data, and use Marvis to determine where some of the issues may have been during a problematic call. This feature has been really helpful for some of my clients who have used it to track down issues with their Teams and Zoom calls. But I have other clients who don't use Teams or Zoom for collaboration and were looking for something similar to this for their various apps. Well, that may still come, but the second big announcement Juniper made was for a Large Experience Model (LEM). This model builds on the data they have gathered and allows the next step of making predictions of application performance. So, rather than just saying "during this call there was a problem because of latency on the WAN link" with the LEM, you can say "it's expected that, based on this network information, calls here will be problematic because of WAN latency". And this predictive capability doesn't require Zoom/Teams integration, nor is it limited to Zoom and Teams applications. And all of this data will be presented in a new Service Level Expectation (SLE) section.
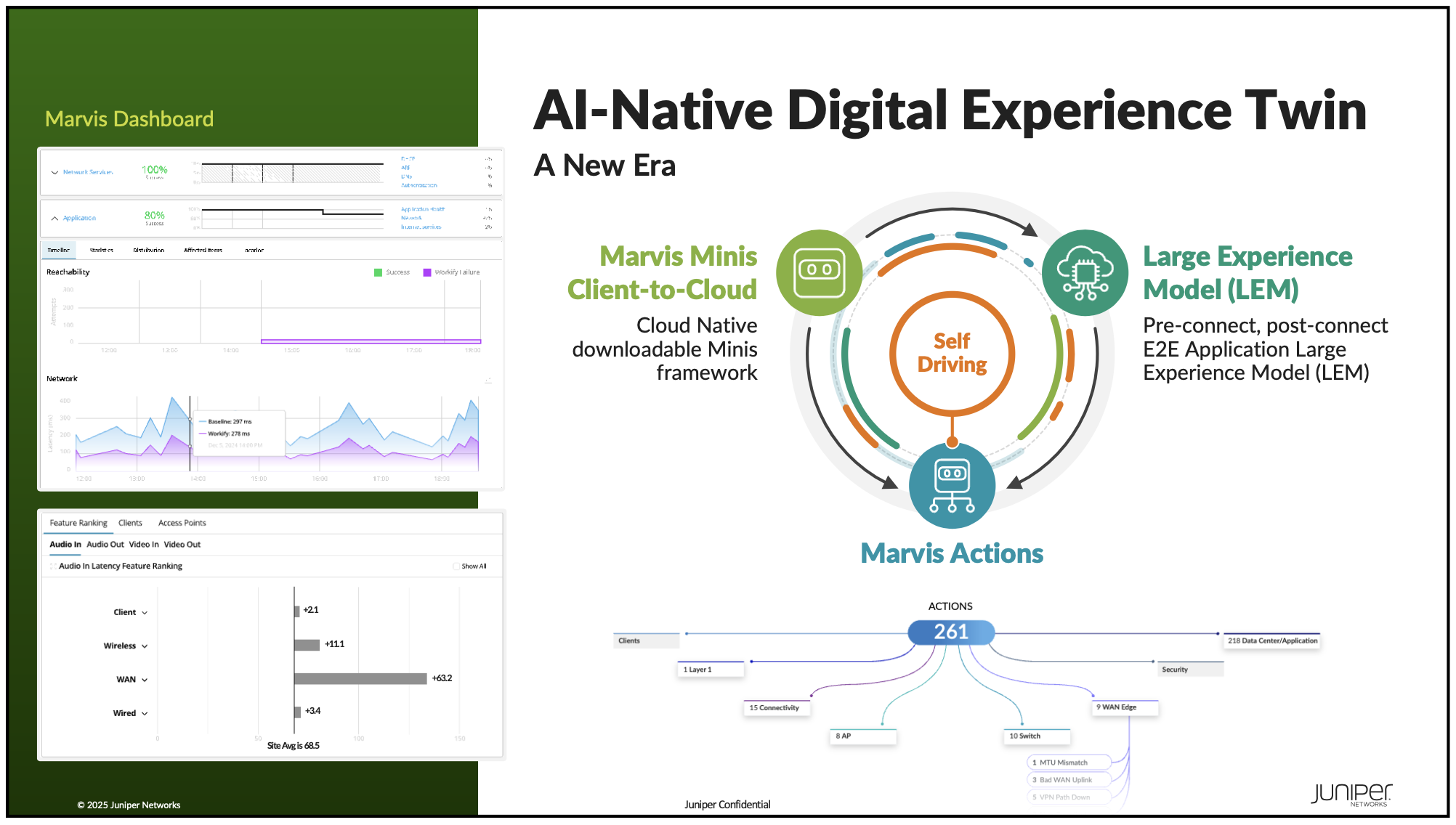 So that's great, but hunting down real-time collaboration issues doesn't sound like the most fun, right? That's where this being a generalized model gets interesting. Because with this model and the previously mentioned Global Minis data, Marvis can now make predictions and suggest actions before a problem occurs. So now, Marvis actions can help you identify issues and make changes to the network to prevent issues with real-time collaboration applications (to start) before the users even experience a problem. That's pretty cool. But in a moment worthy of late-night infomercial TV (and I think it may have been a missed opportunity that they didn't title the section "but wait, there's more"), this feature really helps drive functionality into another feature they announced...
So that's great, but hunting down real-time collaboration issues doesn't sound like the most fun, right? That's where this being a generalized model gets interesting. Because with this model and the previously mentioned Global Minis data, Marvis can now make predictions and suggest actions before a problem occurs. So now, Marvis actions can help you identify issues and make changes to the network to prevent issues with real-time collaboration applications (to start) before the users even experience a problem. That's pretty cool. But in a moment worthy of late-night infomercial TV (and I think it may have been a missed opportunity that they didn't title the section "but wait, there's more"), this feature really helps drive functionality into another feature they announced...
3. Marvis goes self-driving
 There was SO much in Bob's pieces of the presentation on the journey Marvis has taken over the years, but it culminated in Marvis's soon-to-be-released ability to be self-driving. Up until now, Marvis has made suggestions/correlations of actions that need to be taken (aptly called "Marvis Actions"). These actions pointed out problems like bad cables, missing VLANs, and stuck ports. Once the action had been presented, an administrator would need to resolve the problem. And while some think that the recommended actions should stay in the hands of a human administrator, many users have been asking for Marvis to take the next step and start to "just fix it". In fact, last year I was on a LinkedIn live session with Bob and some colleagues, and said I couldn't wait for this capability. This next step, having a network agent that is able to recognize and correct issues all on it's own, is something that we've been looking for, hoping for, asking for, and frankly needing for a long time. While we have systems that can adapt to network changes (like dynamic routing protocols), using an "AI" agent hasn't been trusted. What if it gets it wrong, or has a hallucination, etc? We have seen some third-party "bolt-on" agents be used for some of these things, but not usually within the management system itself.
There was SO much in Bob's pieces of the presentation on the journey Marvis has taken over the years, but it culminated in Marvis's soon-to-be-released ability to be self-driving. Up until now, Marvis has made suggestions/correlations of actions that need to be taken (aptly called "Marvis Actions"). These actions pointed out problems like bad cables, missing VLANs, and stuck ports. Once the action had been presented, an administrator would need to resolve the problem. And while some think that the recommended actions should stay in the hands of a human administrator, many users have been asking for Marvis to take the next step and start to "just fix it". In fact, last year I was on a LinkedIn live session with Bob and some colleagues, and said I couldn't wait for this capability. This next step, having a network agent that is able to recognize and correct issues all on it's own, is something that we've been looking for, hoping for, asking for, and frankly needing for a long time. While we have systems that can adapt to network changes (like dynamic routing protocols), using an "AI" agent hasn't been trusted. What if it gets it wrong, or has a hallucination, etc? We have seen some third-party "bolt-on" agents be used for some of these things, but not usually within the management system itself.
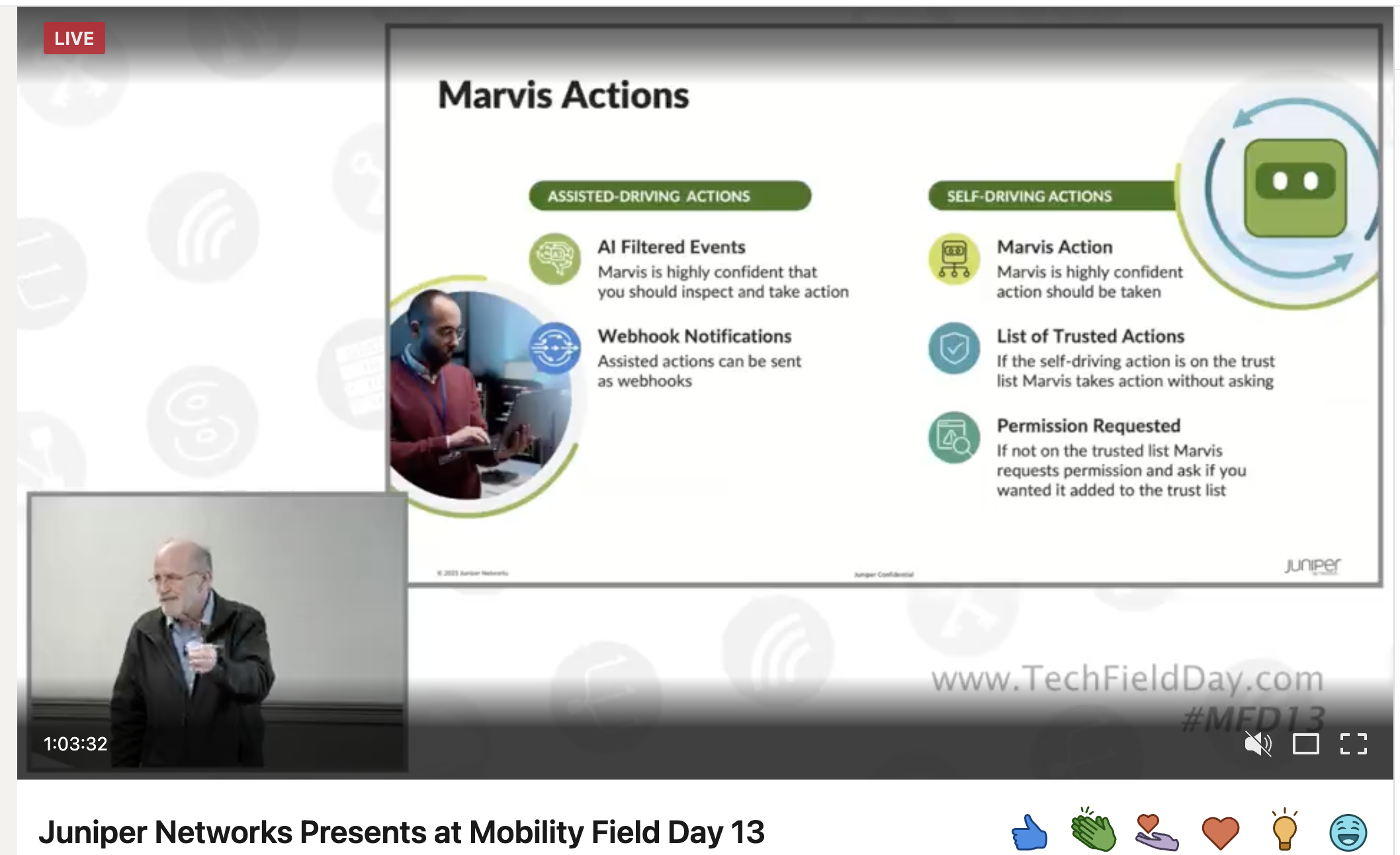 Well, the waiting is over, or soon will be. Marvis is gaining the ability to make changes to the network itself to correct certain issues when they are detected. But rather than just turning Marvis loose on the network, Marvis will gain "Trusted Actions." These are actions that Marvis is highly confident should be taken, and an administrator has added those actions to the trusted actions list. If an action isn't on the trusted list, Marvis will request permission to add it to the list. And while the actions at this initial release may be more limited than some of us would like, looking to the future, there is some real potential here. Issues like a port with an AP connected is improperly negotiated at 100 Mbps (an annoying problem that doesn't take a ton of work to find, but you have to remember to look for it) will be able to be bounced by Marvis to try and force the negotiation up to where it should be. A port missing a VLAN can automatically be configured to add that VLAN. This takes the network truly into the self-driving or self-healing arena. And while there is a way to go before we all take unlimited vacations and just let the network handle itself, this first step is significant to see happening in the management system itself.
Well, the waiting is over, or soon will be. Marvis is gaining the ability to make changes to the network itself to correct certain issues when they are detected. But rather than just turning Marvis loose on the network, Marvis will gain "Trusted Actions." These are actions that Marvis is highly confident should be taken, and an administrator has added those actions to the trusted actions list. If an action isn't on the trusted list, Marvis will request permission to add it to the list. And while the actions at this initial release may be more limited than some of us would like, looking to the future, there is some real potential here. Issues like a port with an AP connected is improperly negotiated at 100 Mbps (an annoying problem that doesn't take a ton of work to find, but you have to remember to look for it) will be able to be bounced by Marvis to try and force the negotiation up to where it should be. A port missing a VLAN can automatically be configured to add that VLAN. This takes the network truly into the self-driving or self-healing arena. And while there is a way to go before we all take unlimited vacations and just let the network handle itself, this first step is significant to see happening in the management system itself.
4. Access Assurance Onboarding Feature With Built-in Certificate Infrastructure (PKI)
 I'll be honest, I loved ALL of the Marvis announcements, but this next announcement came out on top of all of the Juniper announcements for me. It's a two-part "we buried the lead" type of thing. First up, one of the frustrating aspects for many clients is getting devices onboarded to secure networks. This onboarding requires configuring the client's security for the network, generating and installing certificates (you are using EAP-TLS or similar, right? RIGHT?!), and configuring the device to use the network. For company-managed devices that are using a Mobile Device Manager (MDM), it's less of a problem. You set up the configuration in there and push things out. But what about other devices? While other systems allow onboarding of devices, the "ease of use" can be... lacking... (I once had to write 38 pages of instructions for end users on how to onboard their device using a different vendor's NAC system, and those were the EASY version.) And while Mist has had an onboarding portal for pre-shared key (PSK) based networks, so far, there hasn't been anything for the more secure networks. Well, that's about to change. Later this summer, Mist will release a new onboarding workflow that will utilize the Marvis Client to help end users self-provision their device on the network. While the Marvis Client probably deserves its own article someday, the short version is it's an agent package that can be installed on Windows, Mac, Android, and (soon) iOS. This can then provide device-level telemetry and data back to the Mist network. And now it will be extended to include the onboarding of BYOD devices.
I'll be honest, I loved ALL of the Marvis announcements, but this next announcement came out on top of all of the Juniper announcements for me. It's a two-part "we buried the lead" type of thing. First up, one of the frustrating aspects for many clients is getting devices onboarded to secure networks. This onboarding requires configuring the client's security for the network, generating and installing certificates (you are using EAP-TLS or similar, right? RIGHT?!), and configuring the device to use the network. For company-managed devices that are using a Mobile Device Manager (MDM), it's less of a problem. You set up the configuration in there and push things out. But what about other devices? While other systems allow onboarding of devices, the "ease of use" can be... lacking... (I once had to write 38 pages of instructions for end users on how to onboard their device using a different vendor's NAC system, and those were the EASY version.) And while Mist has had an onboarding portal for pre-shared key (PSK) based networks, so far, there hasn't been anything for the more secure networks. Well, that's about to change. Later this summer, Mist will release a new onboarding workflow that will utilize the Marvis Client to help end users self-provision their device on the network. While the Marvis Client probably deserves its own article someday, the short version is it's an agent package that can be installed on Windows, Mac, Android, and (soon) iOS. This can then provide device-level telemetry and data back to the Mist network. And now it will be extended to include the onboarding of BYOD devices.
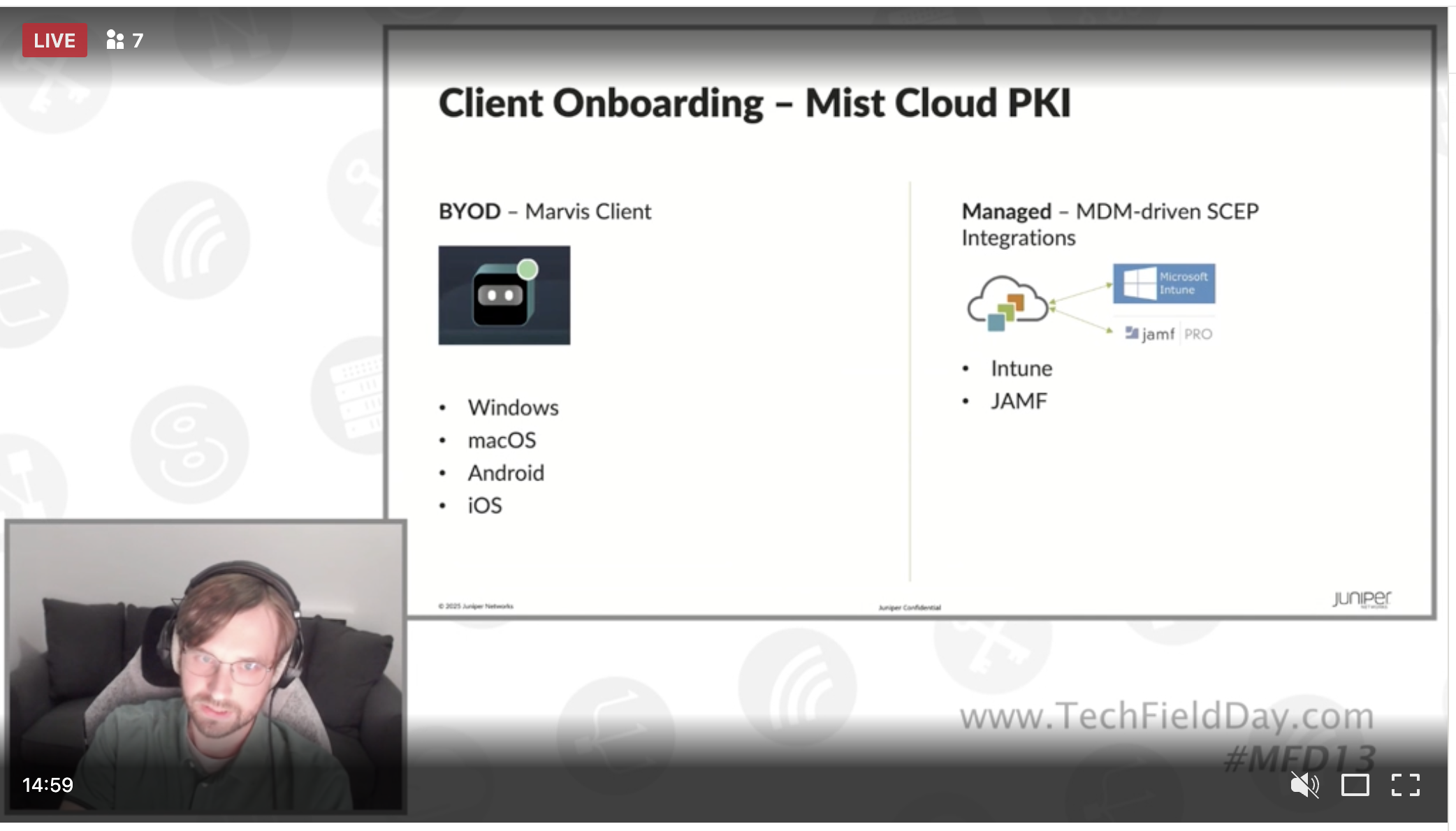 And here we get to the buried lead... Mist Access Assurance will INCLUDE a cloud PKI. For me, this is huge. While I know many folks already have their own PKI implemented (especially if they are using certificate auth for corp devices), Mist greatly benefits from including one in the Access Assurance platform. I have quite a few clients who are outsourcing their certificates to third-party providers (SecureW2, etc). And while it's not necessarily bad, it also comes with a cost. In many cases, a per-user cost. So by adding a PKI directly to the Mist cloud, they can help clients justify the cost for Access Assurance by not needing that external subscription in addition to Access Assurance. We can also then talk about the ease of use for clients trying to separate their PKI for BYOD from their main corporate PKI. Add in the seamless integration for client onboarding, and this really is something I've been waiting for! In the primary use case, for managed devices, you'd still use your MDM to deploy certificates and network configurations, but you can also tie back into the Mist Cloud PKI there. So if you don't have a PKI already set up and running, this will make it easier even for your managed devices.
And here we get to the buried lead... Mist Access Assurance will INCLUDE a cloud PKI. For me, this is huge. While I know many folks already have their own PKI implemented (especially if they are using certificate auth for corp devices), Mist greatly benefits from including one in the Access Assurance platform. I have quite a few clients who are outsourcing their certificates to third-party providers (SecureW2, etc). And while it's not necessarily bad, it also comes with a cost. In many cases, a per-user cost. So by adding a PKI directly to the Mist cloud, they can help clients justify the cost for Access Assurance by not needing that external subscription in addition to Access Assurance. We can also then talk about the ease of use for clients trying to separate their PKI for BYOD from their main corporate PKI. Add in the seamless integration for client onboarding, and this really is something I've been waiting for! In the primary use case, for managed devices, you'd still use your MDM to deploy certificates and network configurations, but you can also tie back into the Mist Cloud PKI there. So if you don't have a PKI already set up and running, this will make it easier even for your managed devices.
5. Posture Enforcement and Device Profiling in Access Assurance
 I'm combining these two because IMO they are so often tied together. Let's start with posture enforcement. The key here is that while Mist has had some level of posture enforcement (via MDM integrations), they are now extending this assessment to Extended Detection and Response platforms from SentinelOne and Crowdstrike. While MDMs can assess posture, they usually only do so periodically (for example, the check-in default for Microsoft Intune is 8 hours). With an EDR tool (if you're unfamiliar with it, think of it as modern antivirus), posture is constantly being assessed. With the integration, the EDR tool can now directly act on the device, notify its central management platform, and notify Mist. Mist can then take action on the network side. Now, how functionally useful is this, you ask? Since most EDR tools can restrict network access, etc, do we really need the network to also take action (like putting it on a quarantine VLAN)? I don't know the answer here. I think in most cases, that will be done on a per-company basis. I don't see it as a problem, and it will likely provide some value in the long run. At the least, I don't think it hurts. Unless, of course, it's taking away from the development of more important features.
I'm combining these two because IMO they are so often tied together. Let's start with posture enforcement. The key here is that while Mist has had some level of posture enforcement (via MDM integrations), they are now extending this assessment to Extended Detection and Response platforms from SentinelOne and Crowdstrike. While MDMs can assess posture, they usually only do so periodically (for example, the check-in default for Microsoft Intune is 8 hours). With an EDR tool (if you're unfamiliar with it, think of it as modern antivirus), posture is constantly being assessed. With the integration, the EDR tool can now directly act on the device, notify its central management platform, and notify Mist. Mist can then take action on the network side. Now, how functionally useful is this, you ask? Since most EDR tools can restrict network access, etc, do we really need the network to also take action (like putting it on a quarantine VLAN)? I don't know the answer here. I think in most cases, that will be done on a per-company basis. I don't see it as a problem, and it will likely provide some value in the long run. At the least, I don't think it hurts. Unless, of course, it's taking away from the development of more important features.
 So now let's talk Device Profiling. Today in Mist, you can see some device details from the network client views. But that isn't used in Access Assurance policies. This new announcement brings another important piece of most NAC systems into Access Assurance. By introducing a fingerprinting service, Mist will take passive data from the network, Marvis Client (if installed), and 3rd Party sources like MDM or EDR tools to create a device fingerprint. This fingerprint will then be shared with Access Assurance and can be used in Authentication Policies. Like other systems, the system will take action if the fingerprint changes (say, in the case of a MAC being spoofed). In the currently announced case, Mist will reevaluate the Auth Policies. I'm not super thrilled that that is the only action currently, though. I'd much rather see the device be tagged and allow the administrator to determine how they want to proceed. Other times when I have implemented NAC, we configured the system to quarantine the device if the profile changes (after the initial profiling). This requires more administrator intervention, but also gives a higher level of confidence and a feeling of security (we could discuss how effective that is as a security practice, but that's for another day). I still want to see something more than "we'll just reevaluate the policies."
So now let's talk Device Profiling. Today in Mist, you can see some device details from the network client views. But that isn't used in Access Assurance policies. This new announcement brings another important piece of most NAC systems into Access Assurance. By introducing a fingerprinting service, Mist will take passive data from the network, Marvis Client (if installed), and 3rd Party sources like MDM or EDR tools to create a device fingerprint. This fingerprint will then be shared with Access Assurance and can be used in Authentication Policies. Like other systems, the system will take action if the fingerprint changes (say, in the case of a MAC being spoofed). In the currently announced case, Mist will reevaluate the Auth Policies. I'm not super thrilled that that is the only action currently, though. I'd much rather see the device be tagged and allow the administrator to determine how they want to proceed. Other times when I have implemented NAC, we configured the system to quarantine the device if the profile changes (after the initial profiling). This requires more administrator intervention, but also gives a higher level of confidence and a feeling of security (we could discuss how effective that is as a security practice, but that's for another day). I still want to see something more than "we'll just reevaluate the policies."
6. Location Services
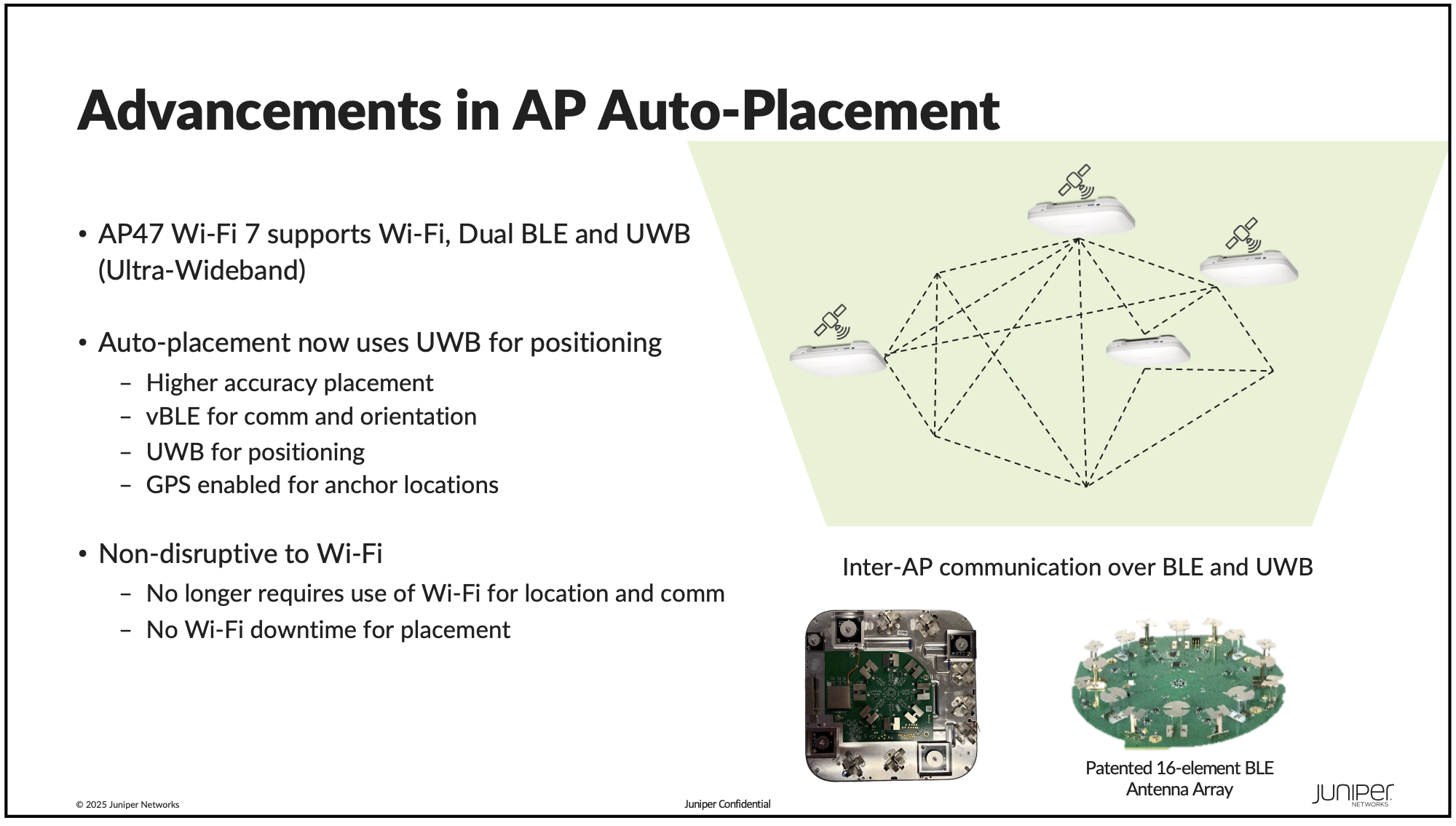 The last section of Juniper's presentation (because they ran out of time) was a good amount of review, but they did highlight a couple of cool features that are in the location services side of Mist. First, they're improving auto-AP placement (the feature where you can tell the system to figure out where the APs actually are on the map and orient them also) to use Ultra-Wideband (UWB) for the new AP47s. This will allow for more accuracy and will remove the Wi-Fi downtime that autoplacement requires on non-UWB APs. The second part that was cool was that they are now using Image Segmentation to automatically generate zones on the floor plans. These zones can be used for a variety of purposes, and now it's even easier for them to be used.
The last section of Juniper's presentation (because they ran out of time) was a good amount of review, but they did highlight a couple of cool features that are in the location services side of Mist. First, they're improving auto-AP placement (the feature where you can tell the system to figure out where the APs actually are on the map and orient them also) to use Ultra-Wideband (UWB) for the new AP47s. This will allow for more accuracy and will remove the Wi-Fi downtime that autoplacement requires on non-UWB APs. The second part that was cool was that they are now using Image Segmentation to automatically generate zones on the floor plans. These zones can be used for a variety of purposes, and now it's even easier for them to be used.
Conclusion
Overall, I don't think any of these announcements are groundbreaking ones like we have seen in the past. HOWEVER, I do think they are all really good, solid improvements and features. Each of them really builds out the Mist platform and value proposition. By making it easier, faster, more straightforward, and integrated to run a Full Stack (truly full stack, meaning WAN, Firewall, Switching, and Wireless) network, Mist increases its value to its end clients and shows why they are continuing to gain momentum in the market.
Watch the Juniper Networks Mobility Field Day 13 Video







